Dr. Alric Althoff successfully defended his PhD thesis “Statistical Metrics of Hardware Security”, which helps answer a fundamental question: How secure is your hardware? This is a difficult task — defining what it means to be secure is something that the computer security field has grappled with for decades.
Dr. Alric Althoff successfully defended his PhD thesis “Statistical Metrics of Hardware Security”, which helps answer a fundamental question: How secure is your hardware? This is a difficult task — defining what it means to be secure is something that the computer security field has grappled with for decades.
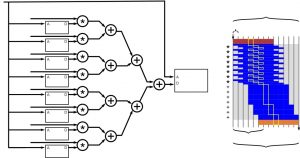
There has been a bevy of high profile attacks on hardware most famously Spectre and Meltdown. It is no longer a question of is your hardware secure (that is easy to answer — it is not), but rather how do we know whether a mitigation technique or run-time vulnerability detection mechanism is effective? Alric developed a set of metrics aimed at answering this question. These metrics enable you to rank when your design is most vulnerable to a power side channel attack, answer questions about the randomness of your random number generator, and determine how hardware optimizations and design decisions affect the leakage of secure information.
While we are on the topic of metrics and definitions, I do not yet know how to define “data science” (nor do I think that term will be properly defined for some time), but I do know that Alric is an exemplar of a data scientist. He is able to quickly understand a problem and come up with elegant solutions to those problems. Thus, it is not surprising that Alric has a been a tour de force for our research group playing prominent roles in almost all of our projects. One of my mantras for the past several years has been “You really should talk to Alric about this.”. His thesis is impressive, and yet this is only a small subset of his research during his PhD tenure.
Luckily (for us) Alric is not moving far; he took a position at Leidos just across the street from campus. Hopefully, we can continue to leverage his expertise going forward.
Congrats Dr. Althoff, best of luck in the future, and don’t be a stranger!
-Ryan