 The latest and greatest version of RIFFA has been released. RIFFA is a framework that enables designers to easily communicate between FPGAs and CPUs over a PCIe bus. This work was born out of immense frustration of building complete hardware accelerated systems. Previous to RIFFA, there was no easy to use way to create an CPU/FPGA hybrid system that could take advantage of the power computing abilities of FPGAs while at the same time utilize the flexibility and interoperability of software running on CPUs. RIFFA changed that and is currently being used by designers around the world.
The latest and greatest version of RIFFA has been released. RIFFA is a framework that enables designers to easily communicate between FPGAs and CPUs over a PCIe bus. This work was born out of immense frustration of building complete hardware accelerated systems. Previous to RIFFA, there was no easy to use way to create an CPU/FPGA hybrid system that could take advantage of the power computing abilities of FPGAs while at the same time utilize the flexibility and interoperability of software running on CPUs. RIFFA changed that and is currently being used by designers around the world.
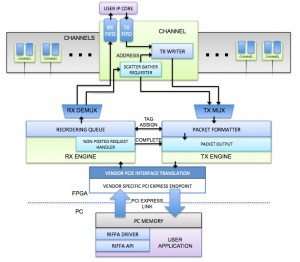
The latest updates to RIFFA include a complete redesign of the FPGA interfacing. This enables user to easily extend it to work with other FPGAs and development boards. The primary developers of this project are Kastner Group PhD alumni Matt Jacobsen and current PhD student Dustin Richmond. The work has been funded by Altera, Intel, and Xilinx. It was the recipient of the FPL Community Award in 2013.
Links:
RIFFA webpage
Xilinx Xcell Daily Blog
UCSD Qualcomm Institute Press Article
UCSD Computer Science and Engineering Press Article
FPL Community Award

