While it took much, much longer than it should have, the semiconductor industry is starting to realize that security is a critical part of the design process. Spector, Meltdown, and other high profile hardware security flaws have shown the danger of ignoring security during the design and verification process. Intel, Xilinx, Qualcomm, Broadcom, NXP and other large semiconductor companies have large and growing security teams that perform audits for their chips to help find and then mitigate security flaws.
Emerging hardware security verification tools (including those spun out of our research group from Tortuga Logic) help find potential security flaws. They are powerful at detecting flaws that violate specified security properties and providing example behaviors on how to exploit the flaw. Unfortunately, fixing these flaws remains a manual process, which is time consuming and often left without a viable solution.
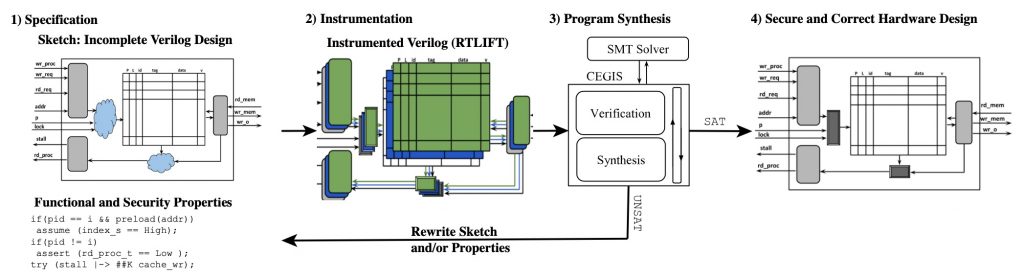
VeriSketch takes a first step at automatically fixing the bugs found by the hardware verification tools. VeriSketch asks the designer to partially specify the hardware design, and then uses formal techniques to automatically fill in the sketch to create a design that is guaranteed to be devoid of the flaw. It leverages program synthesis, which automatically constructs programs that fit given specifications. VeriSketch introduces program synthesis into the hardware design world and uses security and functional constraints for the specification. This allows hardware designers to leave out details related to the control (e.g., partially constructed finite state machines) and datapath (e.g., incomplete logic constructs). VeriSketch uses formal methods to automatically derive these unknown parts of the hardware such that they meet the security constraints.
As a proof of concept, we used hardware security verification tools to show that PLCache (a well known cache that is supposedly resilient to cache side channel) does indeed have a flaw through its meta-data (more specifically the LRU bit). And we were able to use VeriSketch to automatically augment the PLCache design to remove this flaw.
More details on VeriSketch, the PLCache flaw, and other interesting hardware security verification techniques are detailed in our paper “VeriSketch: Synthesizing Secure Hardware Designs with Timing-Sensitive Information Flow Properties” presented at the ACM Conference on Computer and Communications Security. Congrats to the authors Armaiti Ardeshiricham, Yoshiki Takashima, Sicun Gao, and Ryan Kastner!